Researchers at the University of North Texas announced[1] this year on September 24, that they plan to use the 1 million USD, provided by the National Science Foundation, to establish the first framework in the United States that allows self-driving cars to share data with each other. Standardizing the data between self-driving cars is an important infrastructure for achieving “cooperative perception” of the vehicles.
Different brands of self-driving cars use different sensors and software, making it difficult for data sharing between the cars. The Vehicle-to-Everything’s (V2X) purpose is to solve this problem through cloud services using the above framework, so that driving and road information can be transmitted to each other to achieve “cooperative perception”, and make self-driving cars safer. Although this data sharing framework carries many safety and technological benefits, it also establishes a common cybersecurity breach between vehicles of different brands.
V2X cybersecurity issues have been discussed for many years in the automotive industry, academic research institutions and governments. From an industry[2] perspective, Tesla launched the Bug bounty program in 2014 and increased the bonus of the program to $15,000 in 2019. Furthermore, Tesla sent Model 3 to the 2019 Pwn2Own hacker competition, in order to improve the cybersecurity of their products through the power of the masses.
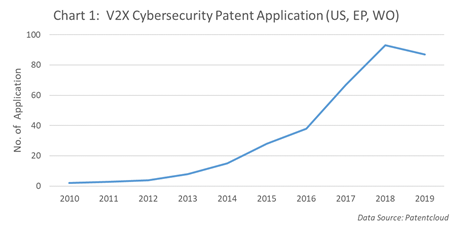
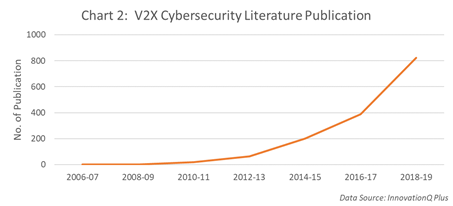
From the statistical data of patents (Chart 1) and non-patent literatures (Chart 2), the number of patent applications and technical/academic publications related to V2X cybersecurity have grown rapidly since 2014 – signs that both industry and academic research have increased their resource allocation in this field. The updated standards and regulations including the international standard ISO/SAE 21434, which was voted[3] for in May of this year, the WP.29 CSMS (Cybersecurity Management System) and SUMS (Software Update Management System), also confirms the importance placed on vehicle cybersecurity, by countries.
Using a vehicle with V2X function comes with its own compromises as it records and sends your location, personal information and entertainment preferences to the cloud. In addition, the contacts and financial information stored in your phone, once synchronized, may also be leaked through the cloud service. Each connection with the vehicle increases the opportunity for hackers to discover loopholes and steal the data through remote access.
More worrying, hackers can use these loopholes to perform remote attacks to take over the control of the vehicle, its seats, heating and cooling, steering wheel, brake, throttle, and engine operation. Clearly, the importance of vehicle cybersecurity is not limited to the vehicle itself. Every environmental infrastructure connected to the vehicle during its journey will become a line of defense for cybersecurity. With the cloud service acting as the brain in the “cooperative perception” process, it will be the core of the defense.
In summary, the importance of V2X cybersecurity should not be underestimated. The author believes, whether it is environmental infrastructure or cloud service providers – in addition to data sharing – manufacturers should also focus on the development of software and hardware for ultimate protection. To gain market share, they need to consider providing products and services that comply with the international standards and regulations (ISO/SAE 21434 and WP.29 CSMS, SUMS), an inevitable future issue for V2X players.
1. Researchers propose industry standard ‘cyber infrastructure’ for autonomous vehicles
https://statescoop.com/researchers-propose-industry-standard-cyber-infrastructure-for-autonomous-vehicles/
2. Tesla is giving a Model 3 away to a hacker who can crack it
https://electrek.co/2019/01/14/tesla-model-3-giveaway-hacker/
3. ISO/SAE 21434
https://www.iso.org/standard/70918.html
4. UN Regulations on Cybersecurity and Software Updates to pave the way for mass roll out of connected vehicles
https://www.unece.org/info/media/presscurrent-press-h/transport/2020/un-regulations-on-cybersecurity-and-software-updates-to-pave-the-way-for-mass-roll-out-of-connected-vehicles/doc.html

